Scripte Windows
This script will completely reset the Windows Update client settings. It has been tested on Windows 7, 8, 10, and Server 2012 R2. It will configure the services and registry keys related to Windows Update for default settings. It will also clean up files related to Windows Upda. Windows PowerShell is an object-oriented automation engine and scripting language with an interactive command-line shell designed to help IT professionals configure systems and automate administrative tasks. You can find it in every modern Windows OS starting with Windows 2008R2.
- Script Windows.location
- Script Windows Update Powershell
- Script Window Size Line 93
- Script Windows Ftp
- Script Windows Key
- Script Windows
You can create a cert to allow you to sign your own Powershell scripts.
Using unsigned scripts requires you to completely disable Windows security measures that protect against running unwanted Powershell code, which would be bad. This method allows you to avoid disabling this code-signed policy.
Everything we do below uses a Powershell prompt, not a command prompt.
Background on certs:
Certificates are given their authority by certificate authorities (CAs). CAs confirm whether or not a certificate is valid. When your computer attempts to use a certificate, it confirms the validity of the certificate by requesting a 'trusted' CA validate the certificate.
You can pay a CA to sign a cert for you, or use a process called self-signing to: create your own CA, then create your own certificate, and then sign your certificate with your own CA.
Windows stores information about which CAs are valid in the certificate store (again, in the 'trusted CA list'). For our purposes this is CurrentUser>Trusted Root Certification Authorities>Certificates.
Separately, Windows stores certificates in the certificate store. For our purposes this is CurrentUser>Personal>Certificates and CurrentUser>Personal>Certificates.
5 Steps total
Step 1: Create your code signing certificate
From a Powershell prompt, run:
New-SelfSignedCertificate -CertStoreLocation cert:currentusermy `
-Subject 'CN=Local Code Signing' `
-KeyAlgorithm RSA `
-KeyLength 2048 `
-Provider 'Microsoft Enhanced RSA and AES Cryptographic Provider' `
-KeyExportPolicy Exportable `
-KeyUsage DigitalSignature `
-Type CodeSigningCert
See the comments section of this article for information about also lengthening the expiration period for the cert (Titus1024).
Step 2: Open the Certificate Manager for Current User
Script Windows.location

From the same Powershell prompt, run:
certmgr /s my
Step 3: Copy the new certificate to the appropriate cert stores
Expand the 'Personal' folder, select Certificates. Right click the new 'Local Code Signing' certificate, and Copy.
Paste into 'Trusted Root Certification Authorities' and into 'Trusted Publishers' stores.
Step 4: Sign your Powershell script with the new cert

From a Powershell prompt, run these two commands:
Script Windows Update Powershell
$cert = @(Get-ChildItem cert:CurrentUserMy -CodeSigning)[0]
Set-AuthenticodeSignature .your-script.ps1 $cert
Step 5: Rerun the Powershell script
You should now be able to run this script without being blocked or prompted about the script being 'unsigned'. You're done!
References
- Cert creation
- New-SelfSignedCertificate
- Windows Certificate Manager
16 Comments
- ChipotleSteven61 May 11, 2018 at 04:17pm
Thanks for a Great Write up, Bookmarked for use later.
- AnaheimASCCC May 11, 2018 at 04:23pm
Does this certificate have an expiration date? Can you set one if it doesn't? Does this get wiped through sysprep?
I've always wanted to do this, but these questions have made it a little harder for me to do so.
- Datildeanmoncaster May 11, 2018 at 04:39pm
I need this thank you! five more words to go
- DatilLarry Shanahan May 11, 2018 at 05:18pm
Good writeup. Maybe give a sentence or two about disadvantages and risks of self-signed certificates? Or even a link to a page where such issues are discussed? I think it would round out the article nicely.
- Ben.B (Spiceworks) May 11, 2018 at 06:49pm
ASCCC,
If you use the exact command I provided the certificate will expire in +1 year from when you create it. Haven't tested with sysprep, but based on this I think the cert would be lost: https://support.microsoft.com/en-us/help/814616/known-issues-that-affect-program-deployment-when-you-use-sysprepLarry Shanahan,
We discussed this somewhat, previously, on the Windows 7 version of this howto - less so 'risks', though. https://community.spiceworks.com/how_to_comment/35261 - Thai PepperPhoenix04 May 11, 2018 at 07:15pm
If you are worried about Sysprep you can always deploy the certificate via group policy.
- Macebbigford May 13, 2018 at 08:51pm
Honestly I never considered going this route because I've always manually set to Unrestricted (as many others have). This is very cool though. I'm going to bookmark this for later.
I did a quick web search and couldn't find a way to lengthen the cert. Something along the lines of maybe 3 years would be nice. October 20th 2020 mac & cheese crawler. 1 year is still very reasonable though.
- SerranoDunc the Punk May 14, 2018 at 02:27am
The sad thing about PowerShell code signing is that the engine doesn't seem to honour PKI. For example, when I created a code signed certificate with my Enterprise CA (which is trusted by all workstations), PowerShell still thinks the signed scripts are untrusted. The actual code signing certificate has to be trusted as per this tutorial.
- Thai PepperDavid Auth May 14, 2018 at 07:05pm
I liked the thumbnail for this article, the ticket was issued to 'Epic Win'. Easy video editor for mac free trial.
Nice write up, bookmarked for future use.
- Macetfl Jul 31, 2018 at 11:32am
Shame this makes you use the GUI.
The trick to signing your cert is to put the cert in both the MY store and the trusted root store. In this sample, the author uses the GUI for the last step. In a perfect worls, there would be a Copy-Certificate cmdlet, but there isnt.
But there is a solution (Bring on .NET!).
# 1 - Create a self signed certificate
$CHT = @{
CertStoreLocation = 'CERT:LocalMachineMY'
DnsName = 'SRV1.Reskit.Org' # change for the name of your server
}
$SSLCert = New-SelfSignedCertificate @CHT# 2. Copy the certificate to the root store on local host
$C = 'System.Security.Cryptography.X509Certificates.X509Store'
$Store = New-Object -TypeName $C ` -ArgumentList 'Root','LocalMachine'
$Store.Open(‘ReadWrite’)
$Store.Add($SSLcert)
$Store.Close() - Ben.B (Spiceworks) Jul 31, 2018 at 02:30pm
Hi tfl, I agree - I looked for a way to complete all of the steps in Powershell, but I couldn't find a built-in method for adding the certs to their respective stores (step 3).
Your step 2 looks like a cool method for doing it!
- SerranoTitus1024 Sep 11, 2018 at 03:57pm
@BBigford 'Honestly I never considered going this route because I've always manually set to Unrestricted (as many others have). This is very cool though. I'm going to bookmark this for later.
I did a quick web search and couldn't find a way to lengthen the cert. Something along the lines of maybe 3 years would be nice. 1 year is still very reasonable though.'
You can extend the cert by adding the parameter -NotAfter (Get-Date).AddYears(3)
This would change the expiration date to 3 years from the day you created it. You can also use -NotBefore to set when the cert becomes valid, I'm not entirely sure what the application of this would be but it's there if you can think of one. - Ben.B (Spiceworks) Sep 11, 2018 at 04:16pm
Very cool additions, Titus1024! I'll add something in the how-to steps to reference your comment.
- PimientoEric6290 Oct 20, 2018 at 12:09am
tfl describes what I need but that does not seem to create a CodeSigning Certificate to add to the stores. It would appear to create a default SSLCertification Cert. Should I still generate the CSC first, separately, and does tfl's step 2 provide certification that the actual CodeSigning Cert is issued by a trusted CA?
A bit lost! - PimientoNix-Mo Sep 16, 2019 at 03:15pm
kind of an old post, but wanted to mention that this should copy the cert for you, assuming you're logged in as a user with elevated rights, and the code-signing cert in your 'My' cert store.
copy-item -path cert:currentusermycertthumbprint -destination cert:localmachineroot

- 1
- 2
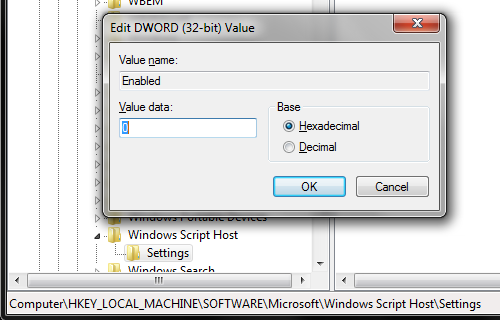
The Windows Script Host service was introduced in Windows 98, and is included with every version of Windows since then. It provides scripting abilities to users, similar to that of batch files, but with more options and features. Having the Windows Script Host enabled in Windows allows users to execute VBScript and JScript files. If you need to enable Windows Script Host, following the steps below.
WarningScript Window Size Line 93
Due to exploitation by some malware programs, Windows Script Host service is often disabled in Windows to prevent security issues.
Script Windows Ftp
Enabling Windows Script Host
- Open the Run or Search menu by either pressing the Windows key or clicking start and locating the white box.
- In the search field, type regedit.exe and press Enter to open the Registry Editor.
- Navigate to the following registry key by clicking through the menus on the left side: HKEY_LOCAL_MACHINESoftwareMicrosoftWindows Script HostSettings
- On the right side of the Registry Editor window, double-click the Enabled registry value.
- If disabled, the Enabled value will be set to 0. Change it to a 1 to enable Windows Script Host.
- Close the Registry Editor window.
Script Windows Key
TipTo disable Windows Script Host, change the Enabled value to a 0.
Script Windows
Additional information

